- SERVICES
- Educate and Alert
- Secure By Design
- Test and Certify
- Automate
- By Industry
- ABOUT US
- …
- SERVICES
- Educate and Alert
- Secure By Design
- Test and Certify
- Automate
- By Industry
- ABOUT US


- SERVICES
- Educate and Alert
- Secure By Design
- Test and Certify
- Automate
- By Industry
- ABOUT US
- …
- SERVICES
- Educate and Alert
- Secure By Design
- Test and Certify
- Automate
- By Industry
- ABOUT US

EDUCATE AND ALERT
The most effective way to ensure success is through consistent training and effort.
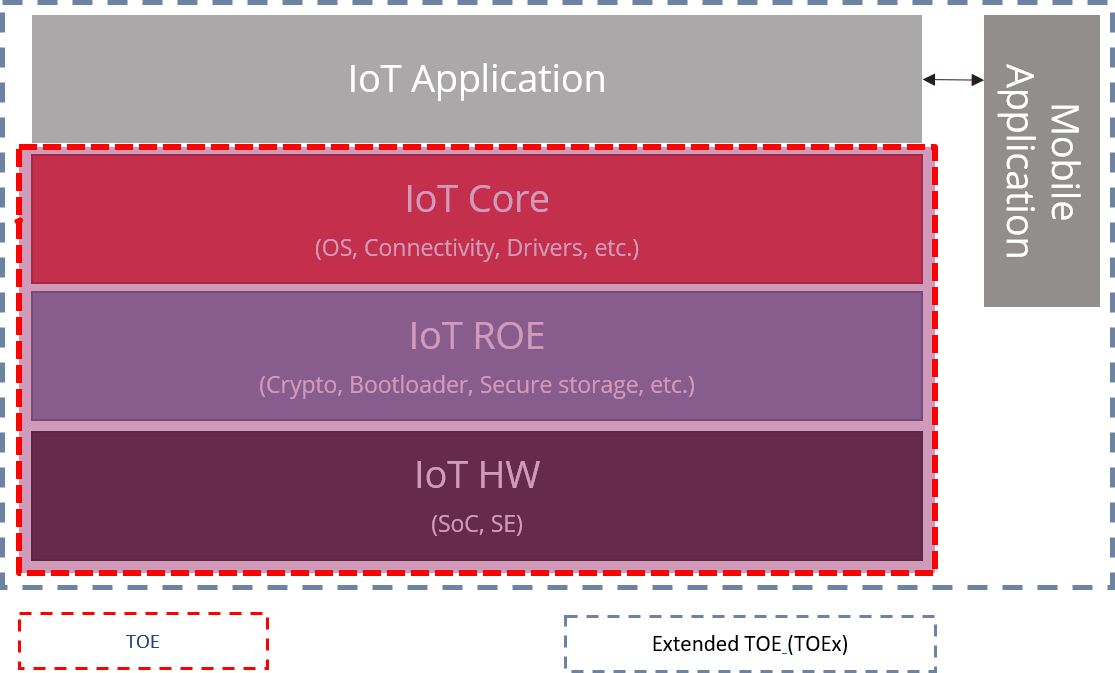
IoT Security Architecture
Internet of Things (IoT) is revolutionizing the way we live and work, but with innovation comes vulnerability. Our IoT Security Architecture Training is designed to equip you with the skills to secure all components of an IoT system. From embedded devices to the cloud, learn to protect each layer against both physical and logical attacks.

What You Will Learn:
- IoT System Components: Understanding various elements of IoT from devices to cloud architectures.
- Designing Secure Communication Protocols: Crafting communication methods that ensure integrity and confidentiality.
- Secure Data Storage and Transmission: Protecting data at rest and in transit with robust encryption and controls.
- Authentication and Authorization Methods: Implementing security checks to verify user and device identities.
- Secure Coding Techniques: Writing and reviewing code with security at the forefront.
- Secure Application Development: Building applications with security integrated from design to deployment.
- Deploying and Managing Secure IoT Products: Mastering best practices for ongoing security management.

Key Benefits:
- Comprehensive insights into IoT security architecture.
- Hands-on experience with real-world scenarios.
- Professional growth and recognition in the IoT security field.
- Networking opportunities with industry experts.
Training Methods
Red Alert Labs training services portfolio, delivered by specialized security experts, provides comprehensive and flexible security training when you need it and how you need it

On-premise training
Get comprehensive and focused in-person training from experienced instructors, and connect with other security professionals.
- Courses are held on our site or at your location
- Full immersive
- Instructor-led
- Tailor-made
- Hands-on exercises for deeper learning through use case scenarios
- Knowledge test

Online Training
Gain knowledge at your desk:
- Online training on demand
- Instructor-led
- Tailor-made online modules
- Hands-on exercises for deeper learning through use case scenarios
- Knowledge test
Why Choose Red Alert Labs ?
Expertise in IoT Security
With a robust background in technology and security, Red Alert Labs brings hands-on expertise specifically in IoT security architecture. Our experts have developed, evaluated, and implemented secure architectures for a multitude of IoT systems across various industries.
Worldwide Recognized Experts & Instructors
Red Alert Labs' team includes specialized experts in IoT security, authors of key industry guidelines, and members of prominent security working groups. Our expertise goes beyond just training; we are at the forefront of IoT security innovations and standardizations.
Influence in Security Standards Development:
As active contributors to IoT security standards, Red Alert Labs has shaped essential frameworks and guidelines within the industry. Our involvement in the creation and adaptation of global IoT security standards ensures that our training is aligned with the latest best practices.
Unique and Proven Training Methodology:
Our approach to training is not one-size-fits-all. At Red Alert Labs, we adapt our teaching methods to suit the unique needs of each audience, ensuring comprehensive, flexible, and in-depth knowledge transfer. Our blend of theoretical insights and practical hands-on experience ensures that participants leave with actionable skills to secure IoT architectures.
Register Now
Secure the future of IoT by mastering its architecture
EU Transparency Register: REG 450926493482-66
© 2025 Red Alert Labs. All rights reserved.